Cyber Security Scans - Part 1
This will be a multi-part blog post, explaining one of our newer services we offer and how we were successful for one customer.
Simply Web Services, LLC, has always offered Cyber Security Scans as a service, but we never really broadcasted it.
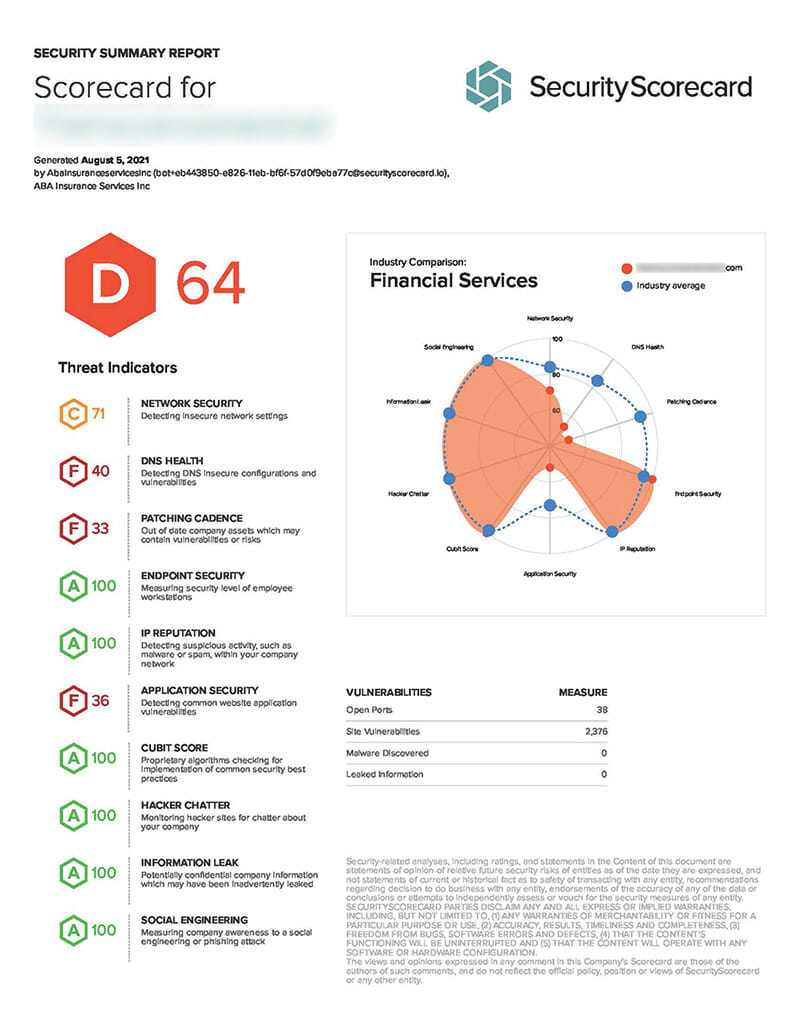
First let me state for the record, that not all Cyber Security scans are created equal, in fact that is their whole marketing point and how they make money. In this case I have a client who I will call “Bob’s Retail Store” with the domain name of “bobsretailsva.com” (all info has been changed to protect the innocent). Due to the nature of some of their business, they are required to have Cyber Security Insurance, and one of the requirements of having Cyber Security Insurance is that they must pass a vulnerability scan. I got an email from the client stating that they failed their scan, with an amazing 64%, with the national average is an 87%. I was shocked to see this low of a result. I take great pride in making sure that my web servers are modern, fast and patched. I work in Cyber Security and I can’t have servers that aren’t patched and full of vulnerabilities.
I told them not to worry, I will dig into the results and get things on the right track.
I created an account on the scanning web site (with the clients permission) and was able to review the whole report first hand. Here are the results from their first scan and what I did to rectify the situation.
There are a total 49 findings in the “NETWORK SECURITY” section
There is 1 high severity finding
There is 1 finding in the in the “SSL/TLS Service Supports Weak Protocol” category being for the IP address that is used by the remote monitoring service
There are 8 medium severity findings
There is 1 finding in the in the “SSH Supports Weak Cipher” category being for the IP address that is used by the remote monitoring service
There is 1 finding in the in the “SSH Supports Weak MAC” category being for the IP address that is used by the remote monitoring service
There are 6 findings in the in the “TLS Service Supports Weak Cipher Suite” category being for the IP address that is used by the remote monitoring service
There are 17 low severity findings
There are 17 findings in the “FTP Service Observed” category, 2 findings for the IP address that is used by the remote monitoring service and 15 associated with other IP addresses on my server that are not related to this web site (this is a shared server with 10 total IP addresses). Not sure how they are pinging on these, however they are not findings related to anything other than I have FTP available, and I will ALWAYS have that available on my servers.
I was able to have all these removed as they are not associated with this clients web site and most are not even on my server. The FTP is considered an acceptable risk as it is a required service and it is locked down as much as it can be for this type of environment. My response was: This is how the customer uploads and modify their website (outside of the CMS), but the FTP service is the latest version of ProFTPd, using SFTP on an obscure port, with Anonymous FTP disabled.
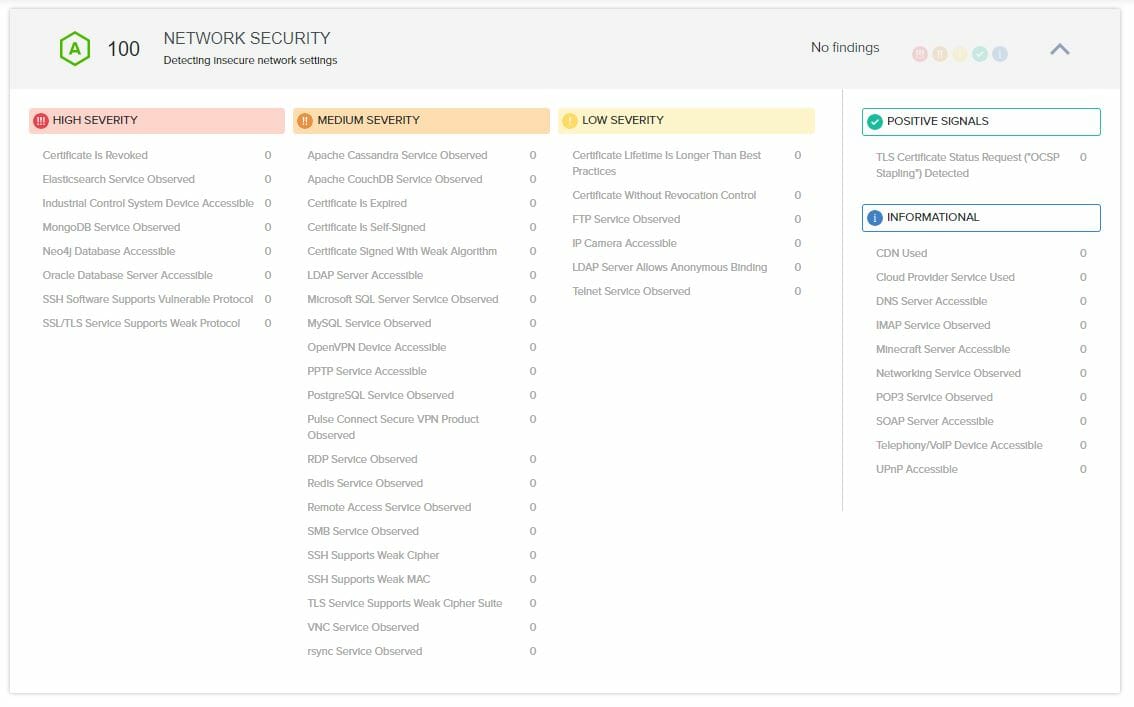
Today the “NETWORK SECURITY” section looks like:
The next post we will continue with the initial scan results.