Cyber Security Scans - Part 2
In our previous Cyber Security Scan post, we started to talk about the findings of the initial scan. Here are the rest of the scan results.
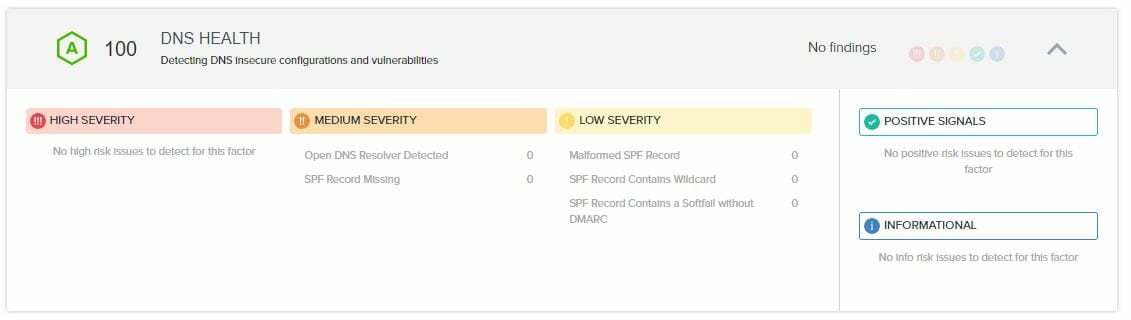
There are a total 87 findings in the “DNS HEALTH” section
There is 0 high severity findings
There are 11 medium severity findings
- There are 11 findings in the “SPF Record Missing” category, they are all related to other websites on my server
There are 76 medium severity findings
- There is 1 finding in the “Malformed SPF Record” category, it is related to another website on my server
- There are 75 findings in the “SPF Record Contains a Softfail” category, they are all related to other websites on my server
So for this particular web site there isn’t any action for this section. I will circle back and clean up the other websites on the server as soon as I complete this effort
Today the “DNS HEALTH” section looks like:
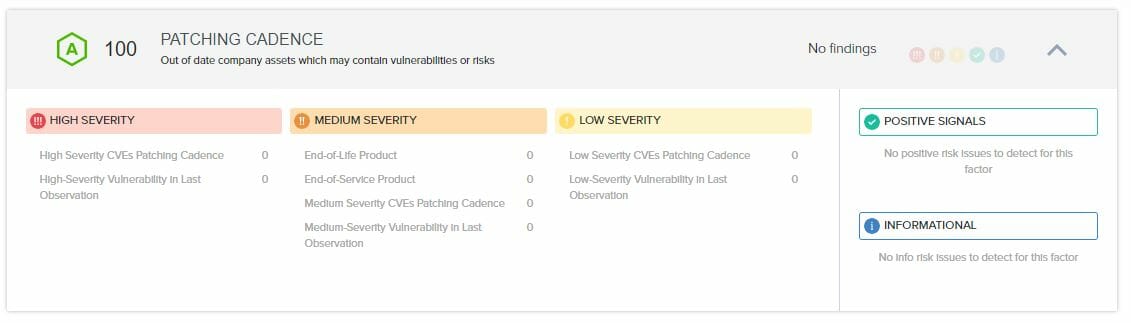
There are a total 811 findings in the “PATCHING CADENCE” section
There are 239 high severity findings
- There are 122 findings in the “High Severity CVEs Patching Cadence” category, 26 findings are on the website, back end, and the rest belong to IP address that is used by the remote monitoring service. I updated the two plug-ins that were out of date (if you operate a WordPress website, you know how quickly a plug-in can get out of date, since there isn’t a standardized release or “patch” day
- Those that deal with the website have been resolved as we were one version behind in my email software. And five that are bogus as they apply to a version of WordPress that you don’t have, you have been upgraded long ago from that version. So they need to figure out what is wrong with their scanner for those five. My Exim installation was version 4.93 and not version 4.94.2, I patched the installation. The five that were bogus, I disputed and they removed (funny as it at this time we were on WordPress core of 5.8.1 and they were referring to vulnerabilities in version 4.7.2. I manually checked each of the referenced files to confirm that they were the correct version
- There are 117 findings in the “High-Severity Vulnerability CVE” category, 109 findings are for the IP address that is used by the remote monitoring service and 8 findings are on my server that related to the previous email software that was one version out of date
There are 528 medium severity findings
- There are 255 findings in the “Medium Severity CVE” category, 46 findings are for the IP address that is used by the remote monitoring service, and the rest being on the DNS server, which has since been upgraded as it was one version out of cycle
- There are 273 findings in the “Medium-Severity Vulnerability in Last Observation” category, a majority are for the IP address that is used by the remote monitoring service, and the rest being on the DNS server, which has since been upgraded
There are 44 low severity findings
- There are 22 findings in the “Low Severity CVEs Patching Cadence” category, 5 findings were for the DNS server (which has been upgraded) and the other 17 vulnerabilities all for the IP address that is used by the remote monitoring service
Today the “PATCHING CADENCE” section looks like:
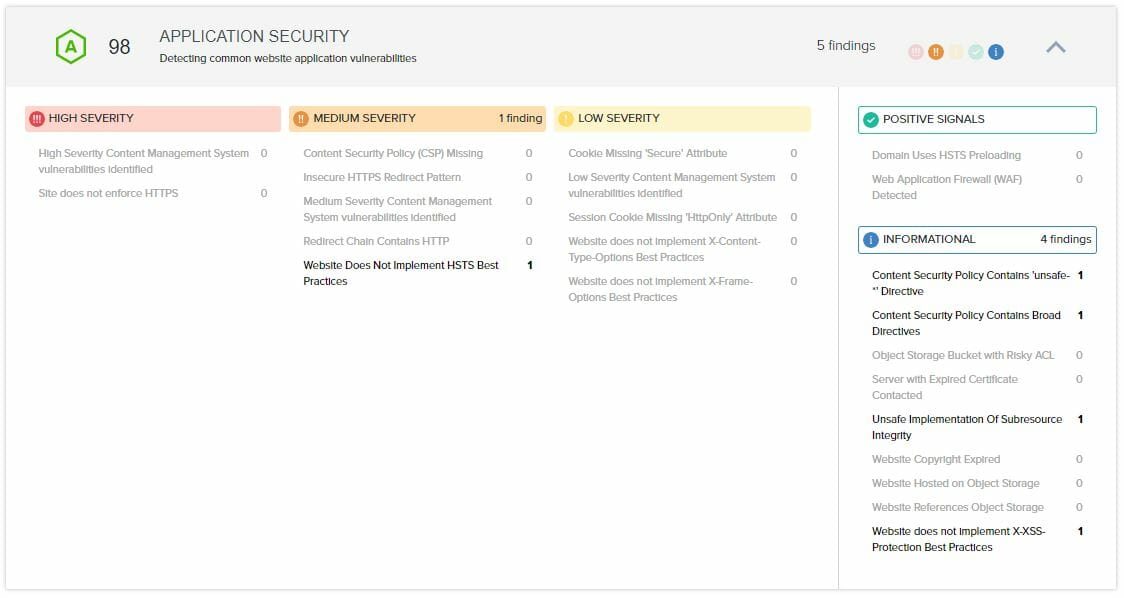
There are a total 2,383 findings in the “APPLICATION SECURITY” section
There are 194 High Severity findings
- There are 194 findings in the “Site does not enforce HTTPS” category, They are all for other websites on my server. I assigned this client’s website a new IP address where they were the only website on it, to help alleviate this silliness
There are 759 medium severity findings
- There are 431 findings in the “Content Security Policy (CSP) Missing” category, these are all for other websites on my server
- There are 48 findings in the “Insecure HTTPS Redirect Pattern” category, the majority are for other websites on my server
- There are 25 findings in the “Redirect Chain Contains HTTP” category, the majority are for other websites on my server
- There are 255 findings in the “Website Does Not Implement HSTS Best Practices” category, the majority are for other websites on my server
There are 948 low severity findings
- There are 90 findings in the “Cookie Missing ‘Secure’ Attribute” category, the majority are for other websites on my server
- There are 29 findings in the “Session Cookie Missing ‘HttpOnly’ Attribute” category, the majority are for other websites on my server
- There are 428 findings in the “Website does not implement X-Content-Type-Options Best Practices” category, the majority are for other websites on my server
- There are 401 findings in the “Website does not implement X-Frame-Options Best Practices” category, the majority are for other web sites on my server
The below are actually, HTTP Header issues with WordPress websites:
- Cookie Missing ‘Secure’ Attribute
- Content Security Policy (CSP) Missing
- Website does not implement X-XSS-Protection Best Practices
- Content Security Policy Contains Broad Directives
- Website does not implement X-Frame-Options Best Practices
- Website does not implement X-Content-Type-Options Best Practices
And to be honest, I have never dealt with this one before, but it was quickly resolved and removed from the results.
Today the “APPLICATION SECURITY” section looks like:
All said and done, they were scanning 47 total IP addresses in 3 countries for some reason. One of the web sites that appeared in the list of vulnerabilities moved away from my server over 10 years ago, talk about a flash back.
Next post I will talk about the remain items in the “APPLICATION SECURITY” section and then wrap this all up.