Let's Go Phishing
Part 1 of 4
Recently, I (Joe) received an email that looked like an email that our email server would automatically send out to an email user.
It came from support@simplywebservices.com, and it was to joe@simplywebservices.com
The subject was “Pending messages couldn’t be delivered, Inbox Full 7/24/2024 10:47:51.“
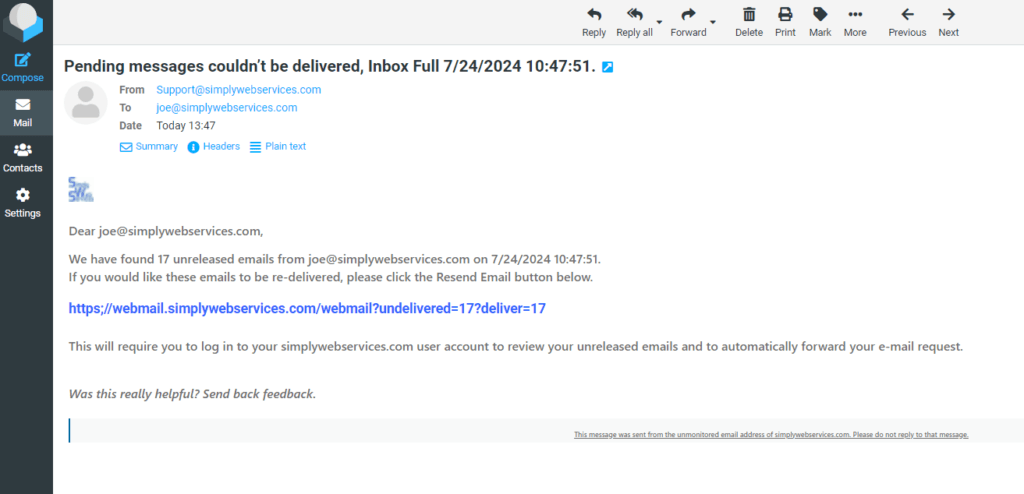
When I clicked on the URL redirected me to https://webmail_286532905.freekasaman.com/527807804cloudstore-#########?data=joe@simplywebservices.com.
(yes, I clicked on the URL, but it was in a controlled environment, where nothing could be infected or hacked).
I was quickly redirected to https://3f32f4.imgloop.com/######.html?em=joe@simplywebservices.com. Of course that was a fake (phishing) website, requesting my email credentials, the phisher was betting that I would enter my email name and password, so they could use it to gain access. (I obfuscated the URLs to protect the innocent)
This was a very realistic-looking phishing email. Here are some things to help educate you so you can recognize something like this in the future.
- The URL isn’t correct. https;// instead of https:// (colon and semicolon)
- The logo is small and grainy (this is because they use a script to grab it and use it on the email, they aren’t checking sizes, in this case, it is our favicon image (which is used when you bookmark a website)
Please note that we use RoundCube for our webmail interface. The URL is always going to be, https://yourdomain.com/webmail