
Email Phishing
Part 4 of 4
Following on the heels of the previous phishing emails, this one is supposedly a HUMAN RESOURCE INTERNAL MEMO, and yep, you guessed it, I’m getting a raise., Yahoooooo!!! It’s about time, lol.
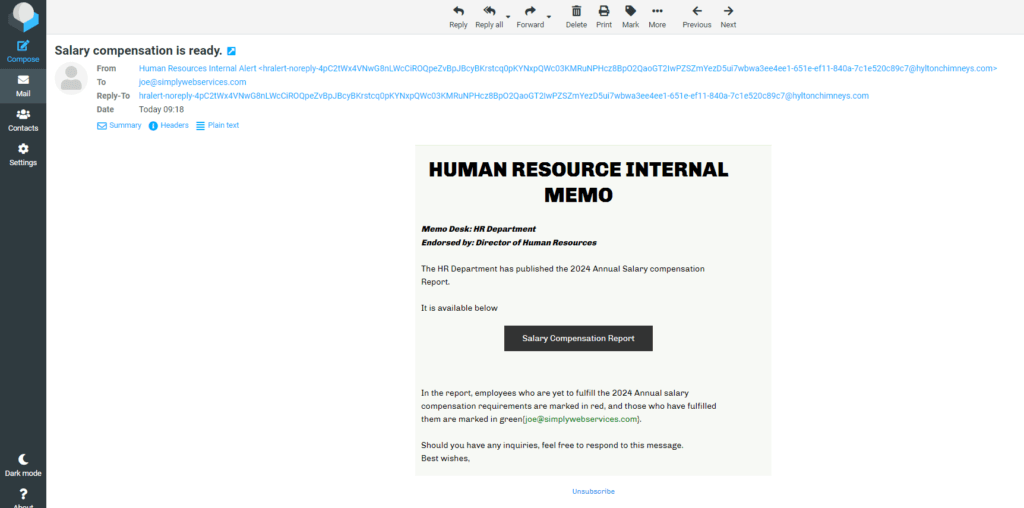
Clicking on the Salary Compensation Report button redirects https://assets-apj.mkt.dynamics.com/######-2d38-ef11-a311-000d3aa0ee9f/digitalassets/standaloneforms/4fd1fc55-4a4b-ef11-a316-000d3aa16cf4#joe@simplywebservices.com which then redirects to https://storage.bhs.cloud.ovh.net/v1/AUTH_d######90534b0e870bed5324cde759/
humanresources/hr-alert.htm#
to a very fancy, animated, and interactive page, where I’m supposed to put in my email username and password. (I obfuscated the URLs to protect the innocent)
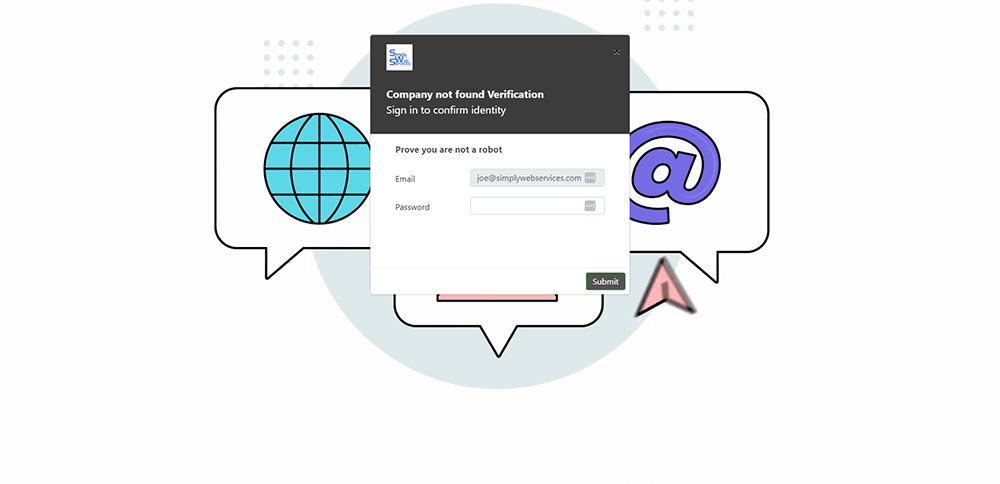
Once I input my username and password (yeah, like I put in my real password), I was redirected to the Simply Web Services home page.
Phishing lessons learned
- We will not send you notice that emails are stuck in the queue
- We will not send you a link to empty your inbox if it is full. We will contact you, but we will not send you a link unsolicited
- Sorry, but there are no salary increases for clients this year, lol
- We are not currently using MS Teams to communicate with clients.